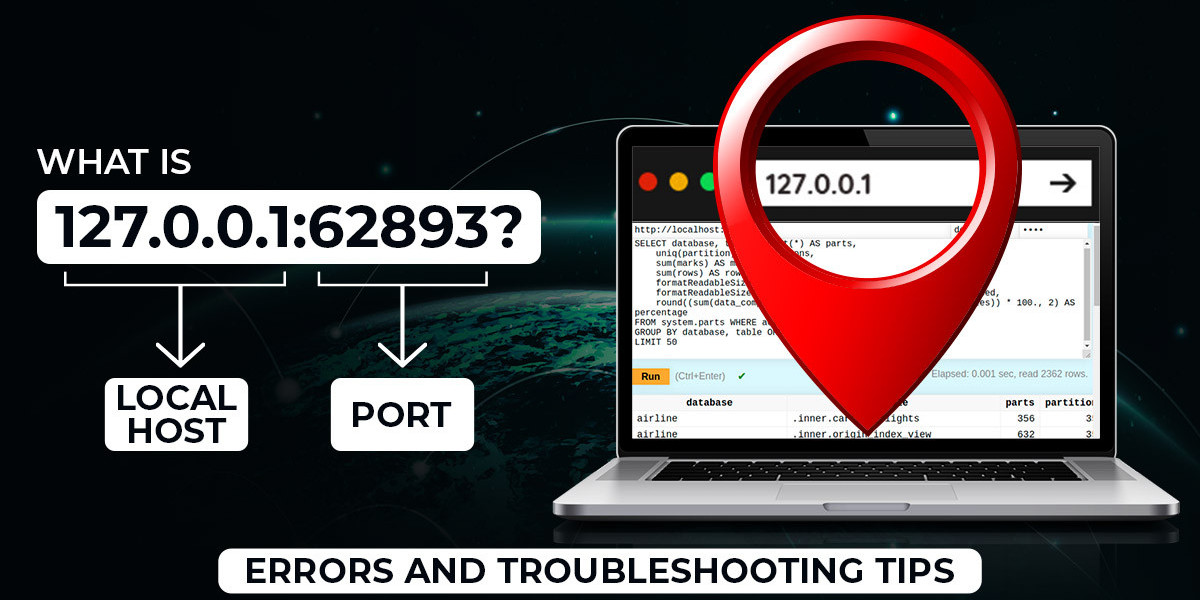
What is 127.0.0.1:62893?
To understand 127.0.0.1:62893, we need to break it down into two components: the IP address 127.0.0.1 and the port number 62893.
127.0.0.1: This is known as the loopback address in Internet Protocol (IP) networking. It's a special address that points back to the host machine. Any data sent to 127.0.0.1 will be redirected back to the same computer. This is typically used for testing and network diagnostics within the local machine.
Port 62893: In networking, a port is a communication endpoint. Port numbers range from 0 to 65535, and they allow different services to run simultaneously on a single IP address. Port 62893 is ephemeral, often dynamically allocated by the operating system for temporary purposes.
When combined as 127.0.0.1:62893, it usually indicates a local service or application running on the host machine and communicating through port 62893. This could be part of a software development setup, a local server for testing, or a background service of an application.
Is 127.0.0.1:62893 Safe?
The address 127.0.0.1 is inherently safe because it confines communication to the local machine. However, safety concerns arise based on what service or application is using port 62893. Here's what you need to consider:
Authorized Applications: Ensure that only trusted and necessary applications are running services on your local machine. Unauthorized or unknown applications using any port might pose a security risk.
Malware: Some malicious software might set up services on random ports, including ports like 62893. Regularly scan your system with up-to-date antivirus software to detect and remove any potential threats.
Firewall Settings: Your firewall should be configured to block unnecessary incoming and outgoing connections. Since 127.0.0.1 traffic stays within your computer, it usually doesn’t need firewall intervention, but knowing your firewall’s configuration can help mitigate risks from misconfigured software.
Troubleshooting Tips
If you encounter issues or have concerns with 127.0.0.1:62893, here are steps to troubleshoot effectively:
Identify the Application: Determine which application or service is using port 62893. On Windows, you can use the command
netstat -ano | findstr :62893to find the process ID associated with this port. On macOS and Linux, uselsof -i :62893ornetstat -nlp | grep 62893.Check the Application’s Legitimacy: Once you identify the application, ensure it is a legitimate and necessary part of your system. If it's something you don’t recognize, research the application or consider uninstalling it.
Review Logs: Most applications that use specific ports have logs. Check these logs for any unusual activity. Logs can typically be found in the application’s installation directory or through the system’s event viewer.
Update Software: Ensure that all your software is up to date. Software updates often include security patches that can protect against vulnerabilities.
Use Anti-Malware Tools: Run a comprehensive scan with your anti-malware tools. If the port usage seems suspicious, this can help detect and remove malicious software.
Configure Firewalls and Security Software: While loopback traffic is generally safe, configuring your firewall to monitor unusual activity on local ports can add an extra layer of security. Ensure your firewall rules are strict but not overly restrictive, to avoid unnecessary disruptions.
Consult Documentation or Support: If the port is used by a known application, consult the application’s documentation or support resources. They might provide specific troubleshooting steps or information on why the port is used.
Conclusion
127.0.0.1:62893 is typically a benign address and port combination used by local applications and services. Ensuring the safety of this port involves knowing what applications are using it and maintaining a secure and updated system. Regular monitoring, appropriate firewall configurations, and up-to-date security software are key to keeping your system safe from potential threats. If you experience any issues, following the troubleshooting tips can help you identify and resolve the problem efficiently.